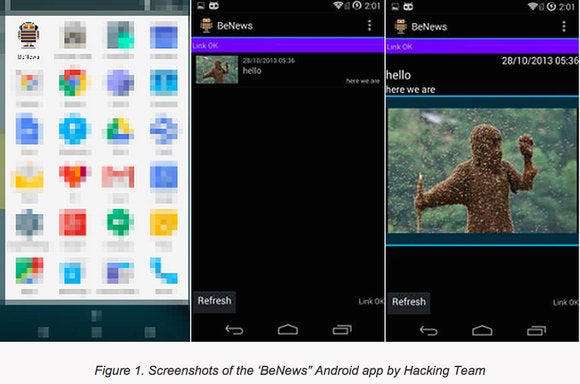
The app, BeNews, only requested three permissions from a user when installed, and was able to avoid Google’s automated app checks as no exploit was contained within its code. One the App was installed, its malicious payload would then snoop on the user and report his/her whereabouts back to the command and control server. This was reported by security research company Trend Micro Labs. Trend Micro said that Hacking Team than sold this App to its customers with instructions to take advantage of the app, and a Google Play account that they could use. The app uses a privilege escalation bug, CVE-2014-3153, found in Android 2.2 to 4.4.4. “Dynamic loading technology allows the app to download and execute a partial of code from the internet. It will not load the code while Google is verifying the app but will later push the code once the victim starts using it.” “No other company has ever produced a lawful surveillance capability nearly as comprehensive, as easy to use, or as powerful as ours.”