The hack attack reportedly targeted the network run by Afghan Ministry of Communications and IT (MCIT) by placing the malicious JavaScript [http:]//cdn.afghanistan[.]af/scripts/gop-script.js in the CDN
The malware downed major Afghan government agencies websites like Foreign Affairs, Finance, Education, Women’s Affairs and Justice and also brought down external website of Australian embassy which used the same CDN network.
[http:]//canberra.afghanistan[.]af/en (Afghan Embassy in Canberra, Australia) [http:]//herat.gov[.]af/fa (Herat Province Regional Government) [http:]//mfa.gov[.]af/en (Ministry of Foreign Affairs) [http:]//moci.gov[.]af/en (Ministry of Commerce and Industries) [http:]//moe.gov[.]af/en (Ministry of Education) [http:]//mof.gov[.]af/en (Ministry of Finance) [http:]//moj.gov[.]af/fa (Ministry of Justice) [http:]//mowa.gov[.]af/fa (Ministry of Women’s Affairs) [http:]//oaacoms.gov[.]af/fa (Office of Administrative Affairs and Council of Ministers)
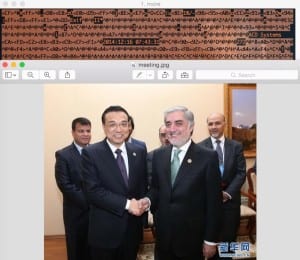
ThreatConnect researchers who analysed the attack, found the watering hole attacks bore a timestamp which coincided with a meeting on infrastructure development and bilateral cooperation in Kazakhstan between China’s Prime Minister Li Keqiang and Afghanistan’s government chief executive officer Abdullah Abdullah. The researchers said an image used to serve the malware was modified only hours after it appeared to be taken at the meeting.
ThreatConnect has named this attack as Operation Helmand and said that this attack was similar to the other hack attacks in South East Asia. It also said that this attack is similar to the June watering hole attack in which a malicious Java file was served on the website of the Greece embassy in Beijing during a diplomatic meeting to Athens. Resource : ThreatConnect